Anarchitecture
About me
Anders Rune JensenMasters from AAU 2006
Worked on secure scuttlebutt for 2-3 years
WARNING
This talk is going to beopinionated!
Application architecture
- Infrastructure / computers
- Data
- User interface
Standard architecture
Features
- Server: hacked, (shut) down
- Data is centralised
- The UI is standardized
- Power lies in being able to decide how the system can be used
- Online - One size fits all usage / moderation
- Company - Reflect existing org hierarchies
Machine learning
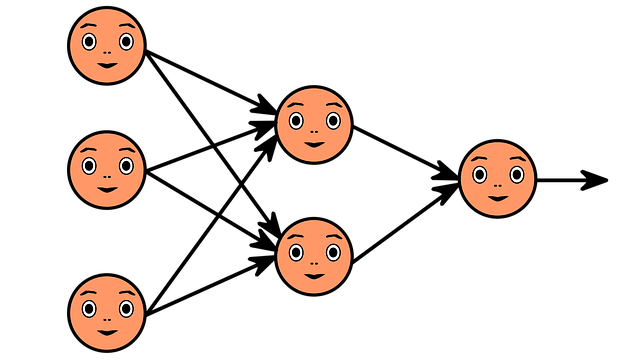

Architecture
Infrastructure / computers- Data
- User interface
ML recommendation systems
- Anywhere with large quantities of data
- Youtube, Netflix, Amazon, Google search, Facebook
- Not on facebook (2.3B)? Android apps interact with Facebook
- King James bible, calorie counter or period tracker
User Interfaces
- Personalized feeds
- More than 70% of view time on YouTube comes from recommendation algorithms
- Data -> UI -> Data -> UI
Is this love?
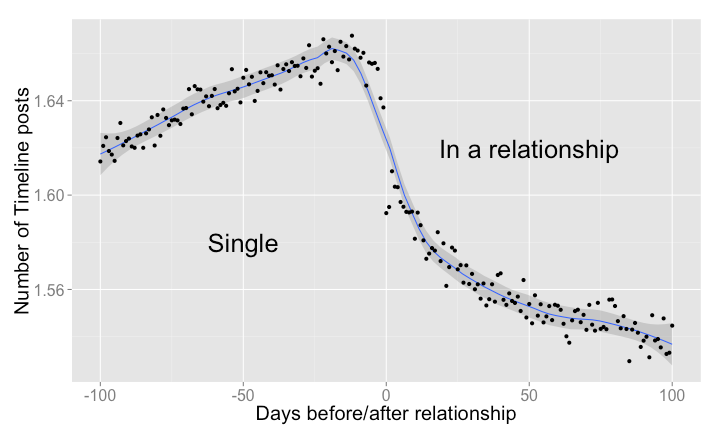
Features
- Give power to the data
- Meaning anyone who can generate
- ... or buy the data
- Black boxes are an attack vector, same as proprietary software
One way of buying is ads
- Facebook, google and twitter have ad libraries
- Riddled with bugs
”They (Mozilla analysts and French officials) found that
identical searches often returned different results, and
that the library became unreliable and often crashed when
they tried to extract large amounts of information.”
Some problems
- Money laundering for bias
- Degenerate feedback loops (echo chambers, filter bubbles) in recommender systems
Tay.ai
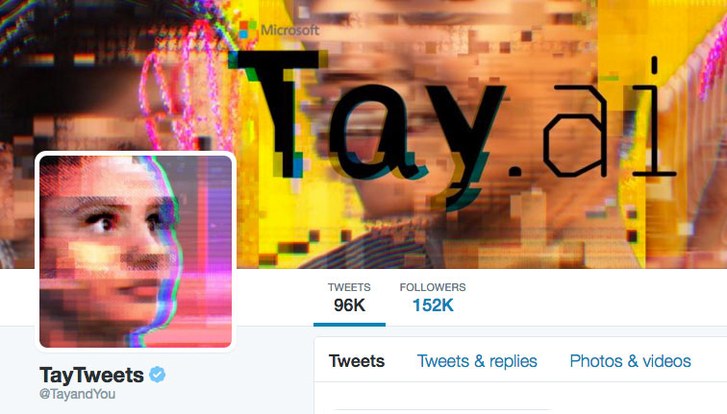
24 hours to turn evil
Opportunity
How Taiwan combats misinformation
”First, before a propaganda campaign or disinformation spreads, we
usually observe that there is a point where they are doing some
kind of limited testing or A/B testing, and that's before it
became really popular. It's just testing the meme, the variation,
to see whether it would go viral, so to speak.”
”Each of our ministries now has a team that is charged to say if
we detect that there is a disinformation campaign going on, but
before it reaches the masses, they're in charge to make within 60
minutes an equally or more convincing narrative.”
Lithuanian elves
- Volunteer based
- Fight trolls spreading misinformation
- Resistance fighters for the 21st century
“We don’t try to be propagandists in reverse. Lithuania has problems, of course, like any nation. We only want to expose the bullshit.”
Danish election 2019
- Advertisement in TV illegal by law
- Advertisement on internet not regulated?
W T F

Ethical questions
- What values does the trained algorithm embody?
- How do we determine this? Is it static?
- Who decides what these values can be?
Machine learning summary
- Individualize
- Propriatary data and algorithms
- Constant battle
P2P architecture
Federated
- Power centralized at servers
- Hacked, shut down
- Benevolent dictator moderation
- Diversity, local governance
- Tendency towards eventual centralisation
Distributed
- Power at the edges
- Users control:
- infrastructure
- data
- software (incl. UI)
- Bottom up governance
Local first software
inkandswitch article:- fast
- multi-device
- offline
- collaboration
- longevity
- privacy
- user control
Scuttlebutt

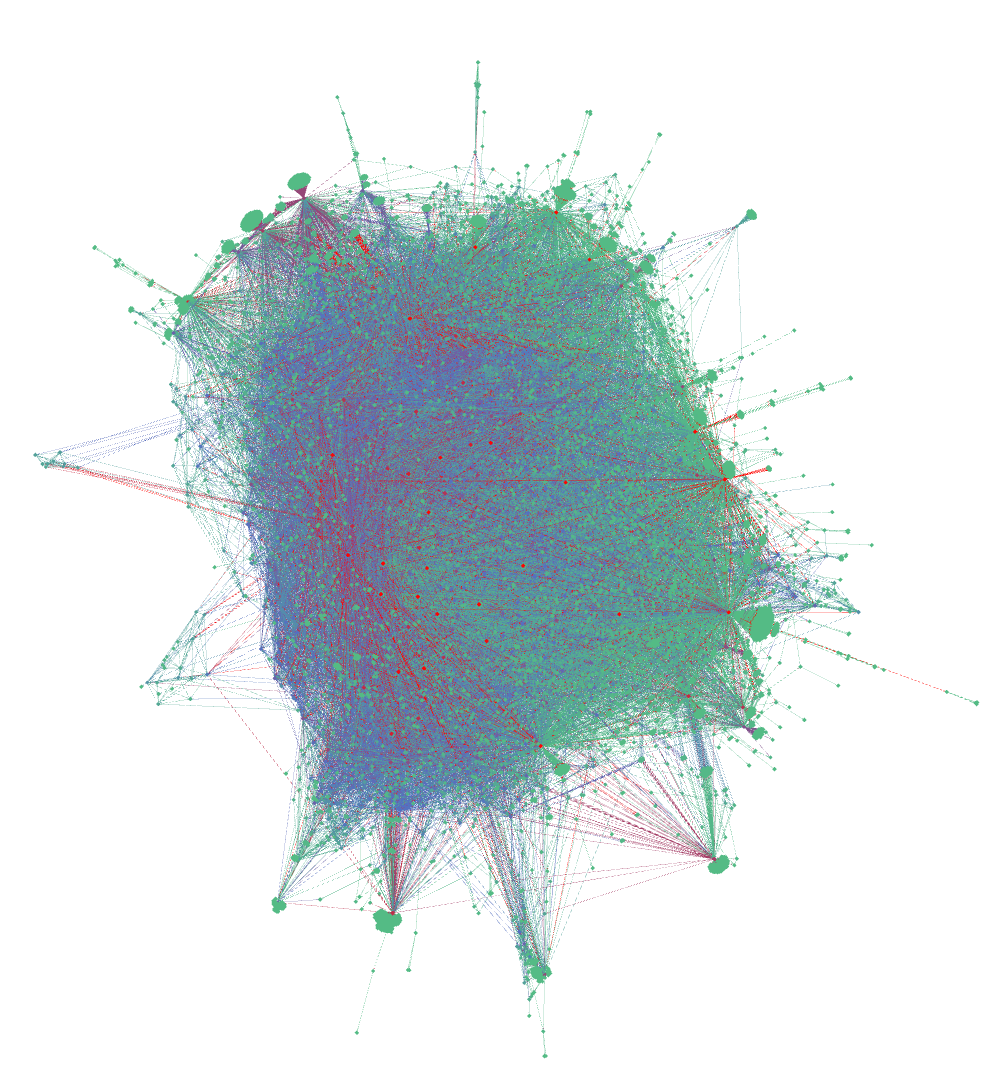
Size is number of incoming connections, red are people with earlier network-birth, blue are newer people.
Scuttlebutt
- Identity centered
SocialFriend network- No gatekeepers
- Data stored locally
- UI embodying local values
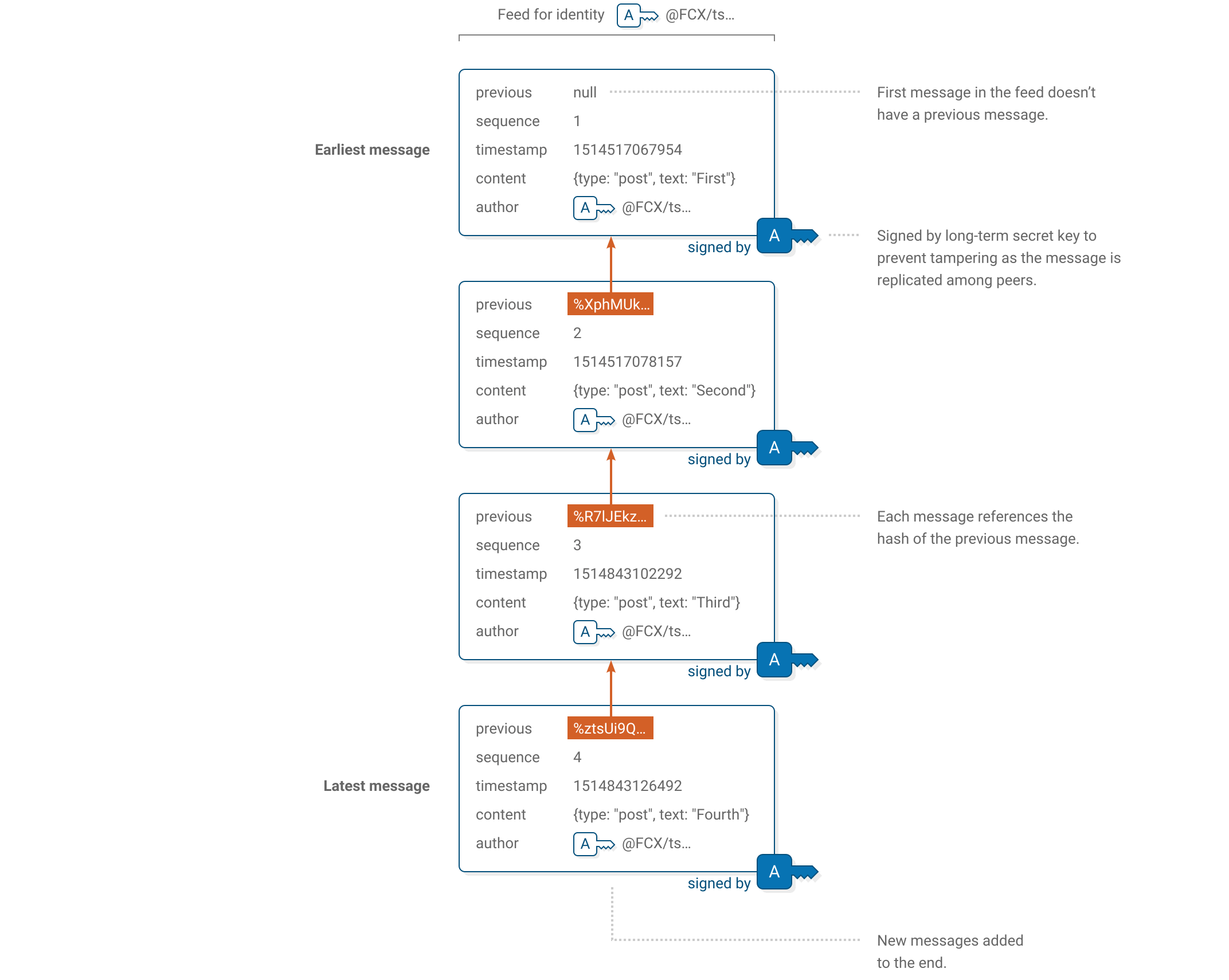
Scuttlebutt feed
SSB
- Event sourcing
- Feeds are chains of immutable messages (8k limit)
- No global ledger consensus
- Public and private messages
- Larger files stored as blobs (5mb soft limit)
- Only you store your private key
Addressed by hash
- Signed and linked messages by hash
- No URL
- Location transparent
Gossipping
- Local network / bluetooth
- Pubs
- Onion hidden services
- Sneakernets
Replication - pull feeds
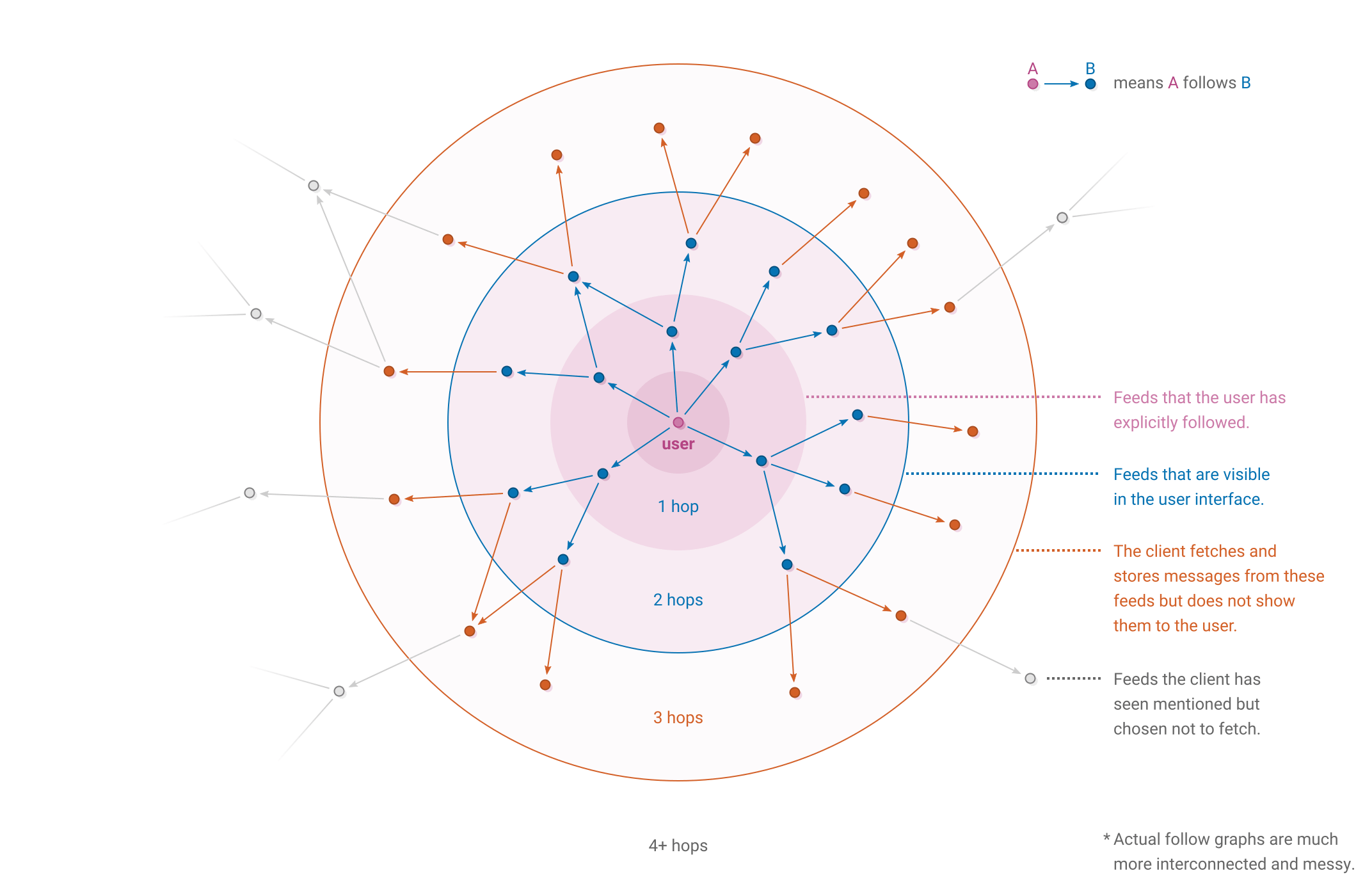
Push updates
- Long running connections
- Epidemic broadcast trees
- Identity based, ordered logs
Blocking
- Following, not (yet) following or blocking
- Friends blocking works for you
- Friend block and other follow then replicate only that feed, not foaf (sybil swarms)
- Blocking deletes local feed data
- Can be private (like contact)
Properties
- Easier to guard against spam / harassment
- Pubs are problematic
- Peer invites rolling out
Caps

Software
- Implementations: javascript, go, rust, c, python
- Multiple interfaces: patchwork, patchbay, patchfoo
- Manyverse - mobile app
Patchwork
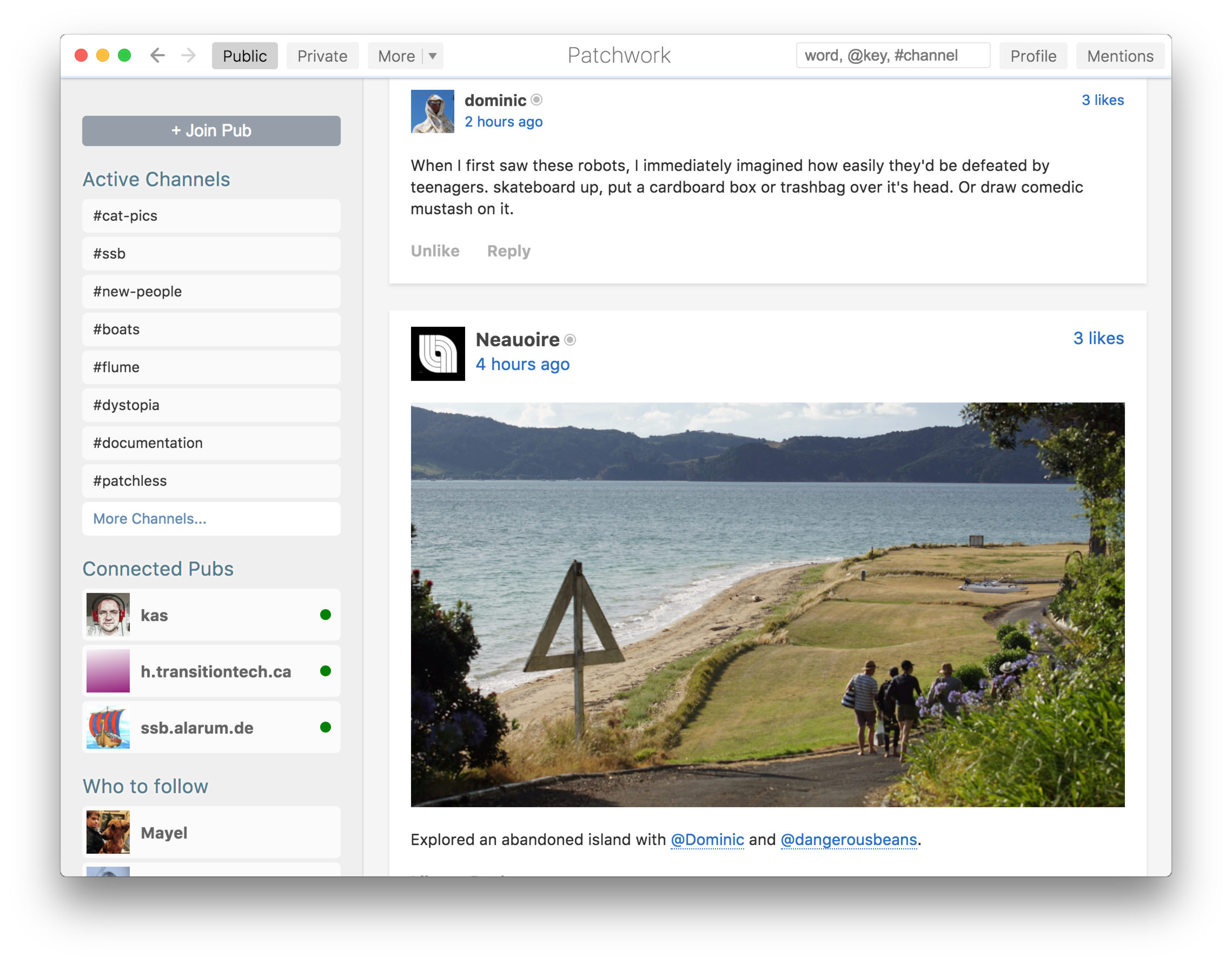
Apps
Book app
- Books are posted as messages
- Can be edited, reviewed by anyone using messages
- Data from your friends & friend of friends
- Local filtering
SSB 💙 Dat
- ssb for social
- dat for files
- pubs seeding dats from friends
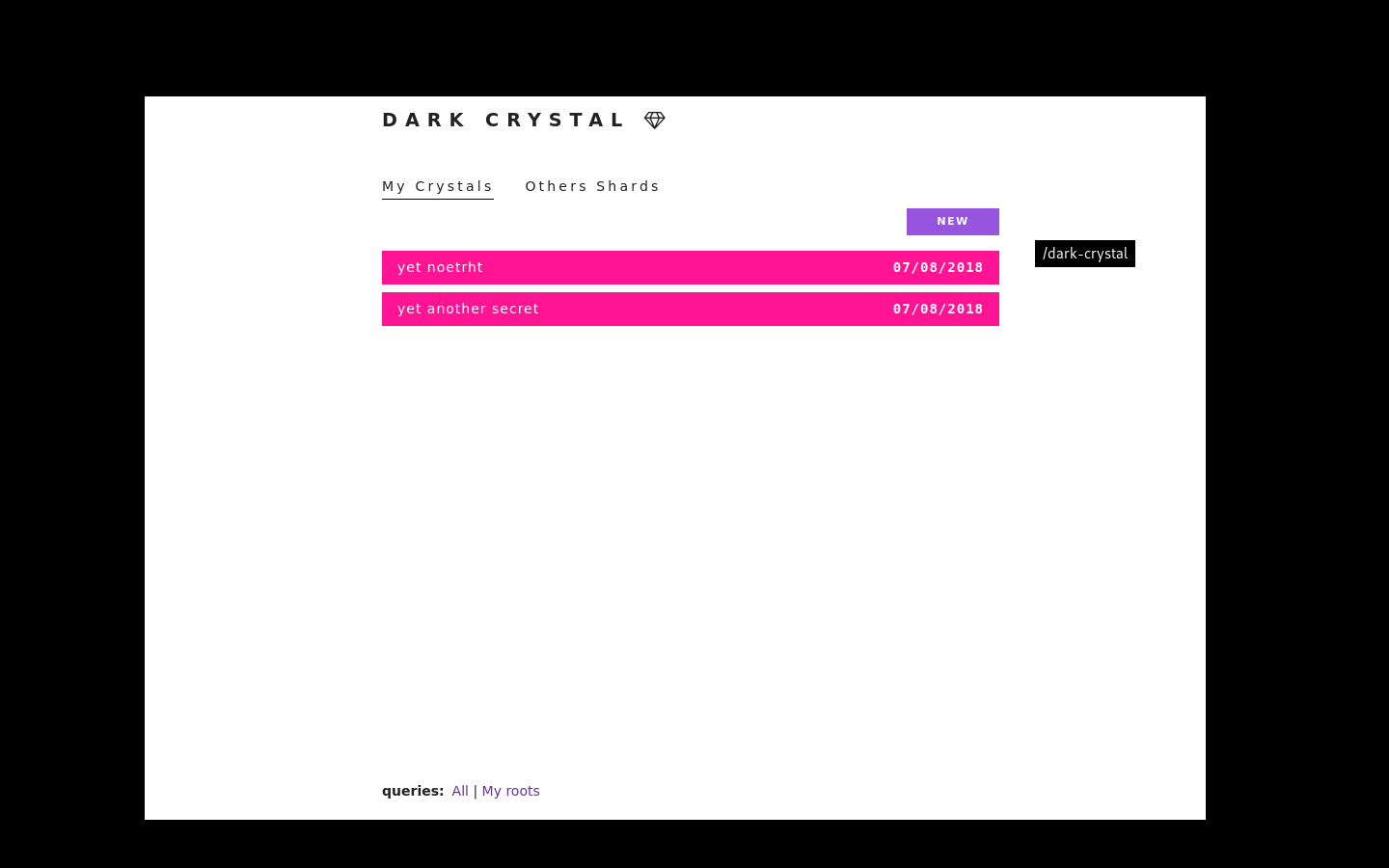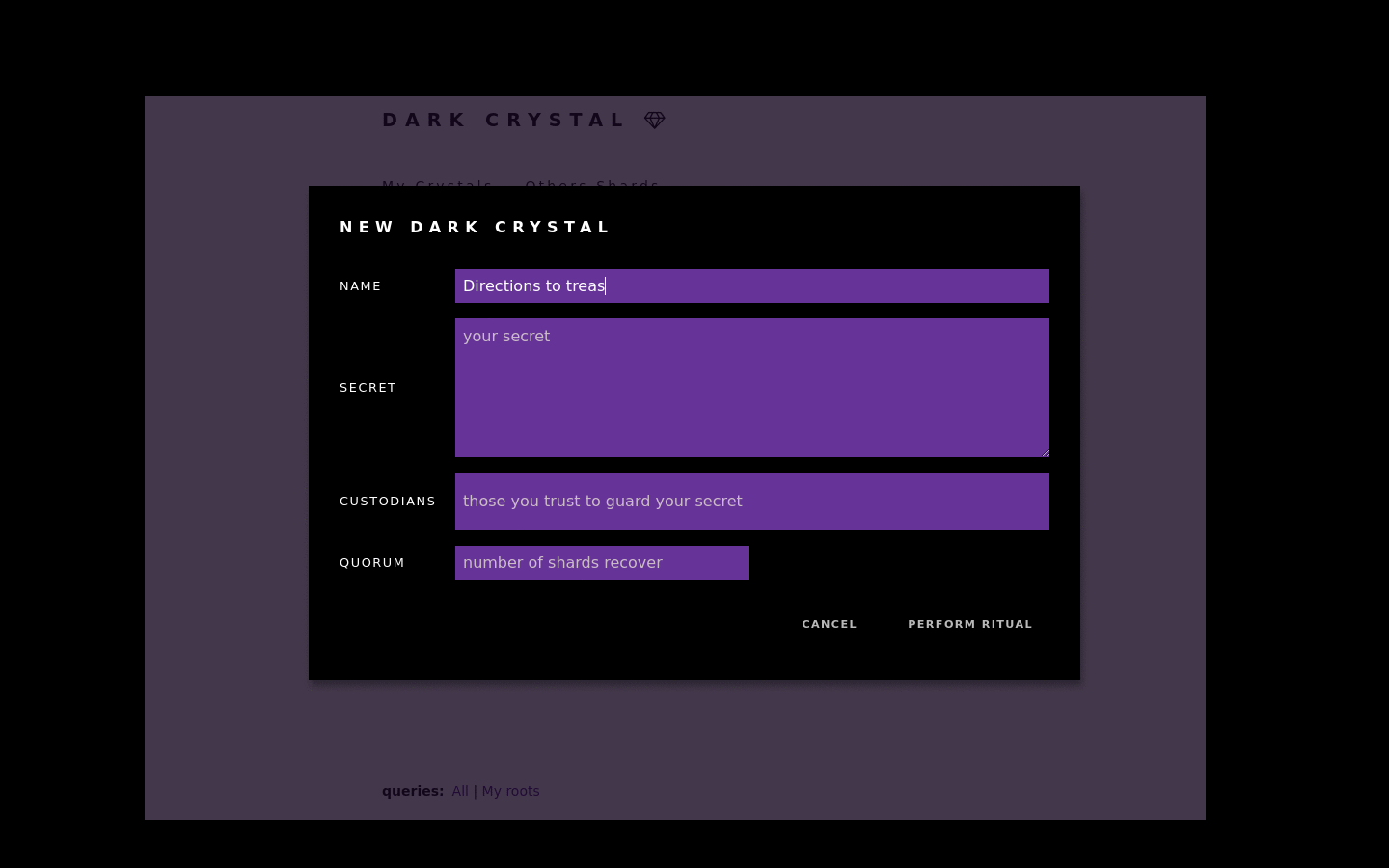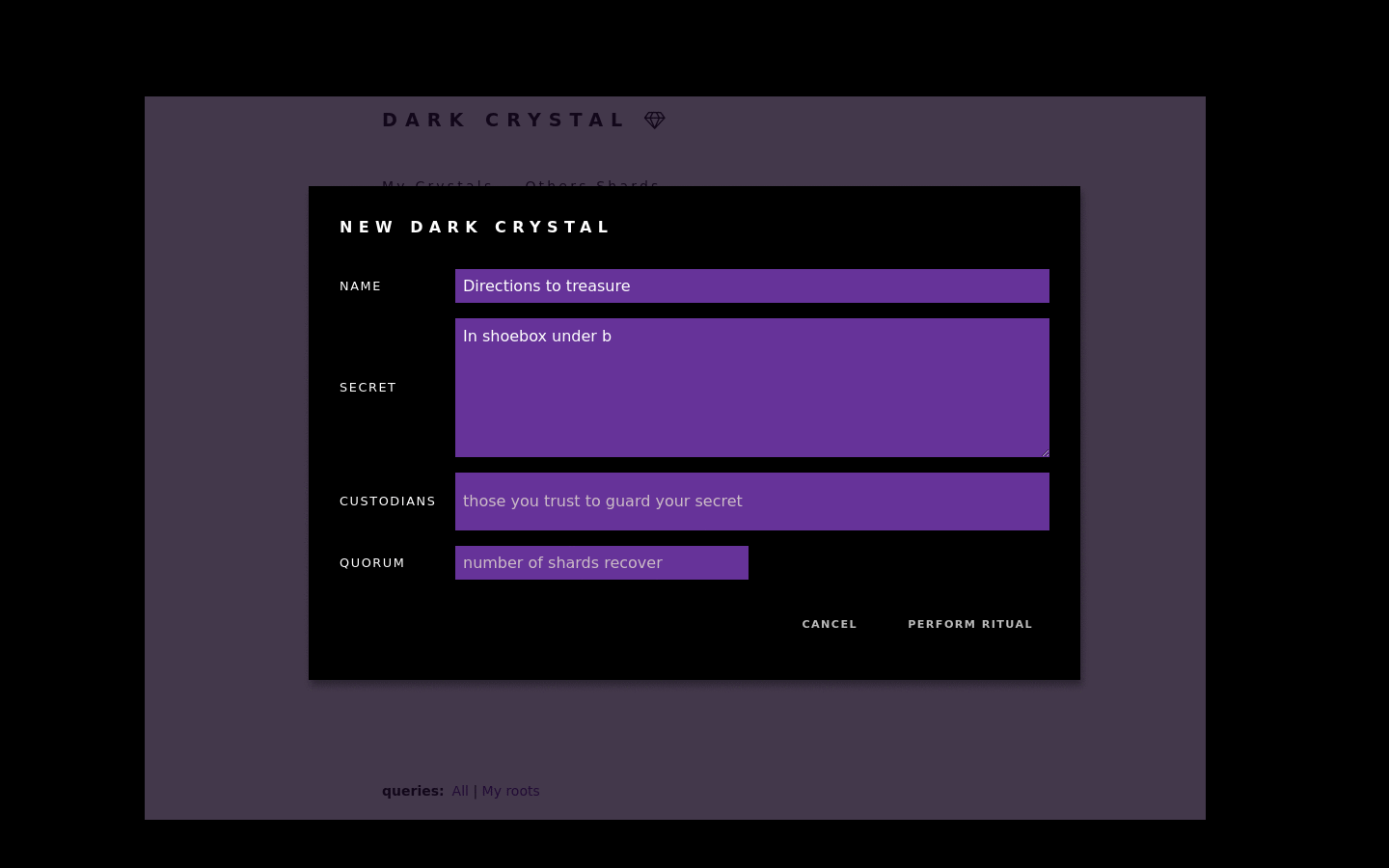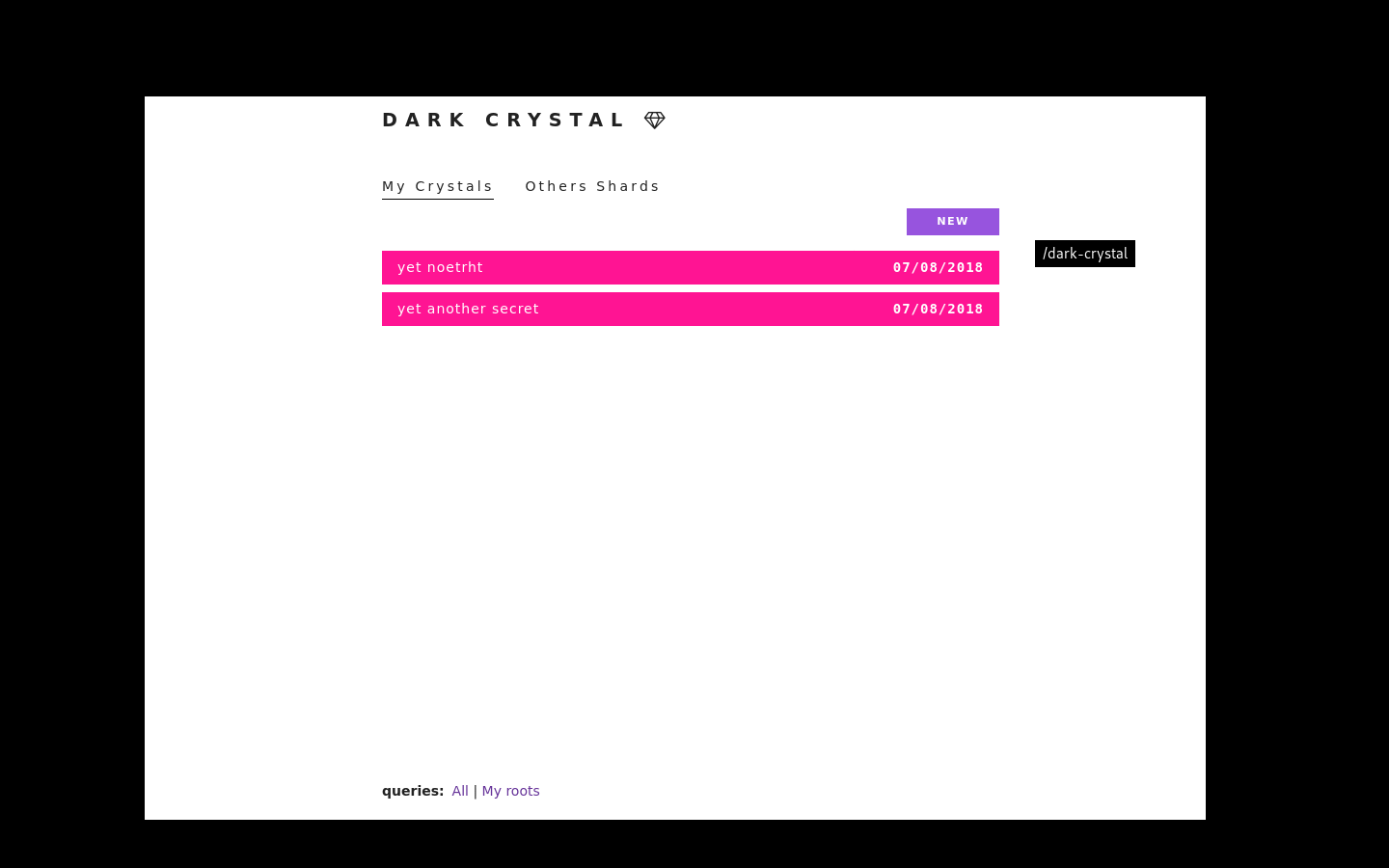
Dark crystal
Git-ssb
- git init
- git add hello-world.js
- git ssb create ssb ssb-lite
- git push --tags ssb master
Created repo: ssb://%jfJAj+ssx9p9N85IN3Y00e3mXPqyYHKhShTeNwMap1w=.sha256 (ssb-lite)
Pushing blobs...
Published %al9oi9okem6YM5vbb/eh3L4e6h+dW8y9phvEFBfspOE=.sha256
To ssb://%jfJAj+ssx9p9N85IN3Y00e3mXPqyYHKhShTeNwMap1w=.sha256
Pushing blobs...
Published %al9oi9okem6YM5vbb/eh3L4e6h+dW8y9phvEFBfspOE=.sha256
To ssb://%jfJAj+ssx9p9N85IN3Y00e3mXPqyYHKhShTeNwMap1w=.sha256
About a month ago
 Konstantin Ryabitsev - Linux foundation
Konstantin Ryabitsev - Linux foundation

Currently brewing
- New message format
- Private groups
- Full peer in browser
- Safer spaces (abuse audit)
Demo
Egalitarian software
- People run the infrastructure
- User in control of their data
- Subjective data views
- Not a technological solution to social problems

High modernism
High modernism is a form of modernity, characterized by an unfaltering confidence in science and technology as means to reorder the social and natural worldCharacteristics
- 1950-1960
- Centralization
- Rationalization
- (Over)simplification
- The end justifies the means
Chicago
Bruges
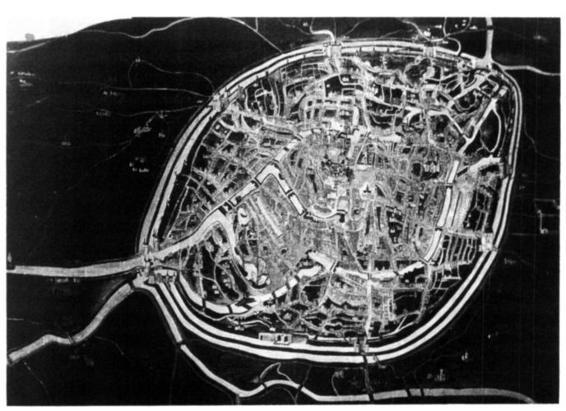
Digital high modernism
- Computers are a modernists wet dream
- Top down approach
- Systems enforcing (simple) rules
China

Mall camera
 Tiny frame-mounted cameras analyze your face, discerning your
age, gender and mood
Tiny frame-mounted cameras analyze your face, discerning your
age, gender and mood
Digital panopticon
1925
Global surveillance
-
State:
- Chinese social credit system
- NSA - Snowden Capitalism:
- Silicon Valley - Google, Facebook, Twitter etc.

Barcelona
Value technical sovereignty
”We believe that data is a public infrastructure”
”Vodafone, the provider of the city’s telecoms services,
is now contractually obliged to give back the data it
collects from the public, which will be published
anonymously on the
council's open
data portal. It wasn’t exactly easy to
negotiate: They resisted for over a year”
- Early Chinese Manual of Governance
Summary
- Architectures: centralised, decentralized and distributed
- Power: hierarchical, machine learning, egalitarian
- Digital high modernism
Thank you!
Local pub @ BornHack
SSID: meshtheplanet